Tech
-

Enhancing Precision in Sheet Metal Fabrication
Introduction Achieving precision in sheet metal bending is critical for quality and efficiency in modern fabrication. Accurate bends reduce material…
Read More » -

How to Choose the Best Aspect Ratio for Portable Gaming Monitors
Portable gaming monitors are an absolute blessing for gamers who want a way to play with the sharpest picture quality…
Read More » -

Understanding Modern Bending Systems in Fabrication
Introduction to Metal Bending in Manufacturing In modern fabrication, bending is a fundamental process that transforms flat metal sheets into…
Read More » -
Is this the best route planner software of 2026?
If you’ve been carrying a territory for a while, you know the ugly truth: most “planning” happens in the driver’s…
Read More » -

Which Methods Best Measure Plasma Protein Binding?
Accurately measuring plasma protein binding (PPB) is crucial in pharmaceutical development. It informs scientists how a drug interacts within the…
Read More » -
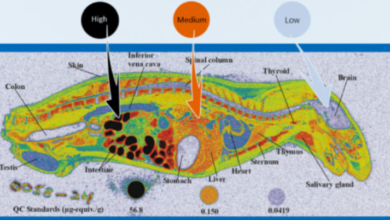
ADC Service Workflow: From Antibody to Cytotoxic Conjugate
ADC service workflows describe how antibodies are transformed into targeted cytotoxic therapies through defined, connected steps. Each stage addresses specific…
Read More » -

How Can You Achieve the Best Out of Your Wedding Video Editor?
Have you ever wondered how your wedding video becomes so beautiful? Your raw emotions seem like a cinematic story with…
Read More » -

Top 7 Digital Marketing Courses That Build Real Portfolio Proof in 2026
Digital marketing roles reward people who can turn research into campaigns and dashboards that influence revenue. The correct course should…
Read More » -

Top 7 Cloud Computing Courses for Business Leaders Who Want Real Multi-Cloud Skills in 2026
Cloud transformation is now a core business capability. Teams that understand cloud architecture, security, and cost control move faster, scale…
Read More » -

The Next Generation of Encryption Algorithms Explained
Introduction to Modern Encryption Encryption is a key part of digital security. It protects sensitive information by converting it into…
Read More »
